
|
Deutsch |

|
Deutsch |
As a venture capitalist who invests in high tech, I have to worry that the web will be perceived as an increasingly corrupt police state overlying a maze of dark alleys and unsafe practices outside the rule of law. The public and many corporations will be reluctant to embrace a technology fraught with such problems. The Internet economy will continue to grow, but it will do so at a much slower pace than forecast by industry analysts.
Jacques Vallee, The Heart of the Internet, p. 162
In 1970–1971 I used to live in a really bad neighbourhood. In the space of two years I was held up three times, twice by the same guy. (One's sense of etiquette fails in such circumstances—what do you say: “New gun?”) Once I found a discarded sofa cushion outside my apartment building and, being perennially short on seating for guests, rescued it from the trash man. After bringing it inside and whacking it to liberate some of the dust prior to vacuuming, I heard a little “ker-tink” sound on the floor. Three times. These turned out to be caused by .22 calibre bullets whose entry holes were visible upon closer examination of the pillow. I know not whether this ballast was added while it was sitting on the sidewalk or in the apartment of the neighbour who threw it away. The sound of gunfire wasn't all that rare on Saturday nights there, then.
Looking back on that time, I don't recall any sense of chronic fear or paranoia, but there's a low level edginess which slowly grinds you down. Now, I could have gotten a large, intimidating dog, put bars on the apartment window and motion detectors inside with triple deadlocks on the door, a concealed carry permit and suitable heat to pack, Kevlar vest for going out after dark, etc., etc. Instead, immediately I received a raise which permitted it, I decided to get out of Dodge, as it were, trading 50% higher rent for a sense of security which freed me to worry about career-related matters instead of whether my career was about to be abruptly truncated due to collision with rapidly moving metallic projectiles.
I've come to view today's Internet as much like the bad neighbourhood I used to inhabit. It wasn't always that way—in fact, as recently as a few years ago, the Internet seemed like a frontier town—a little rough on the edges, with its share of black hats, but also with the sense of open-ended possibility that attracted pioneers of all sorts, exploring and expanding the cutting edge in all directions: technological, economic, social, political, and artistic. But today's Internet isn't a frontier any more—it's a slum. (I use “Internet” here to refer to the culture of the Web, E-mail, newsgroups, and other services based upon the underlying packet transport network. I have nothing against packet switching networks in general nor the Internet infrastructure in particular.)
What's it like living today in the Internet slum? What comes down that pipe into your house from the outside world? Here's a snapshot, taken on March 31st, 2004, a completely typical day in all regards. The Web site racked up 682,516 hits in 56,412 visits from 44,776 distinct sites (IP addresses), delivering 14.8 gigabytes of content. That's, of course, not counting the traffic generated by the Distributed Denial of Service Attack underway since late January 2004. Whoever is responsible for this attack bombarded the site with a total of 1,473,602 HTTP request packets originating from 1951 hosts all around the world. These packets were blocked by the Gardol attack detector and packet blocker I spent much of February developing instead of doing productive work. Well, the attack this day was only half as intense as during the first wave in January. Entirely apart from this recent denial of service attack is the routine attack against Earth and Moon Viewer in which robots attempt to overload the server and/or outbound bandwidth by making repeated requests for large custom images. This attack has been underway for several years despite its impact having been entirely mitigated by countermeasures installed in October 2001; still they keep trying. This day a total of 3700 of these attacks originating from 342 distinct hosts were detected and blocked.
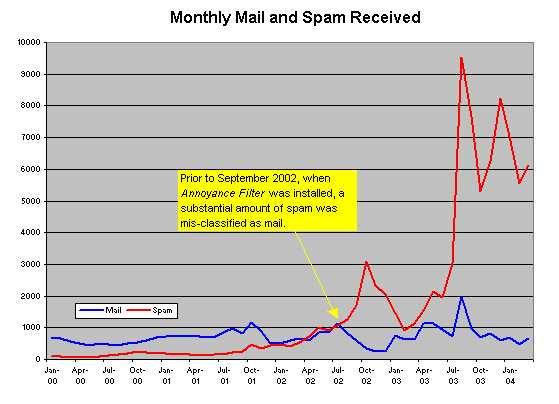
Moving from the Web to that other Internet mainstay, E-mail, let's take a peek at the traffic on good old port 25. This day I received 8 E-mail messages from friends and colleagues around the globe. Isn't E-mail great? But that's not all that arrived that day…. First of all, we have the 629 messages which were blocked as originating at IP addresses known to be open SMTP relays which permit mass junk mailers to forge the origin of their garbage. Open relays, whether due to misconfiguration or operated as a matter of principle by self-described civil libertarians, are the E-mail equivalent of leaving a live hand grenade in an elementary school playground. A peek at the sendmail log shows a total of 6,444 “dictionary spams” attempted that day. These are hosts which connect to your mail server and try names from huge lists of names culled from directories used by spammers in the hope of hitting a valid address which can be sent spam and then re-sold to other spammers. A total of 275 E-mail messages made it past these filters into the hands of sendmail for delivery, being addressed to a valid user name in my domain, usually the E-mail address which I take care not to publish on any of my Web pages. Of these, a total of 259 were correctly identified as spam by Annoyance Filter, the adaptive Bayesian junk mail filter I spent two months developing in 2002 instead of doing productive work. A total of 8 junk mail messages were “false negatives”—misclassified as legitimate mail by Annoyance Filter (in all likelihood because I hadn't recently re-trained the filter with a collection of contemporary spam) and made it to my mailbox. This day's collection of junk mail included a total of 74 attempts to corrupt my computer with destructive worm software, thereby to enlist it in further propagating the corruption. Since the machine on which I read mail uses none of the vulnerable Microsoft products these programs exploit, they pose no risk to me, but consider how many people with computers which are at risk without the filtering tools and the more than 35 years of computing experience I bring to the arena withstand this daily assault. This day there wasn't a single criminal fraud attempt to obtain my credit card number or other financial identity information; this was a light day; usually there's one or two. Absent the open relay block list and Annoyance Filter, I would be forced to sort through a total of 896 pieces of junk mail to read the 8 messages I wish to receive. Isn't E-mail great?
Ever since 1996, when a dysfunctional superannuated adolescent exploited a vulnerability in the ancient version of Solaris I then ran on my Web server to break into the server and corrupt my Web site, I've kept the local network here at Fourmilab behind a firewall configured with all the (abundant) paranoia I can summon. A firewall not only protects one against the barbarians, but monitoring its log lets you know which tommyknockers are knocking, knocking at your door and what keys they're trying in the lock. One doesn't bother logging the boring, repetitive stuff, but it's wise to keep an eye peeled for new, innovative attacks. On this day, the firewall log recorded a total of 1915 packets dropped—the vast majority attempts to exploit well-known vulnerabilities in Microsoft products by automated “attack robots” operated by people who have nothing better to do with their lives. That's about one every 45 seconds.
Imagine if there were a tunnel which ran into your basement from the outside world, ending in a sturdy door with four or five high-security locks which anybody could approach completely anonymously. A mail slot in the door allows you to receive messages and news delivered through the tunnel, but isn't big enough to allow intruders to enter. Now imagine that every time you go down into your basement, you found several hundred letters piled up in a snowdrift extending from the mail slot, and that to find the rare messages from your friends and family you had to sort through reams of pornography of the most disgusting kind, solicitations for criminal schemes, “human engineered” attempts to steal your identity and financial information, and the occasional rat, scorpion, or snake slipped through the slot to attack you if you're insufficiently wary. You don't allow your kids into the basement any more for fear of what they may see coming through the slot, and you're worried by the stories of people like yourself who've had their basements filled with sewage or concrete spewed through the mail slot by malicious “pranksters”.
Further, whenever you're in the basement you not only hear the incessant sound of unwanted letters and worse dropping through the mail slot, but every minute or so you hear somebody trying a key or pick in one of your locks. As a savvy basement tunnel owner, you make a point of regularly reading tunnel security news to learn of “exploits” which compromise the locks you're using so you can update your locks before miscreants can break in through the tunnel. You may consider it wise to install motion detectors in your basement so you're notified if an intruder does manage to defeat your locks and gain entry.
As the risks of basement tunnels make the news more and more often, industry and government begin to draw up plans to “do something” about them. A new “trusted door” scheme is proposed, which will replace the existing locks and mail slot with “inherently secure” versions which you're not allowed to open up and examine, whose master keys are guarded by commercial manufacturers and government agencies entirely deserving of your trust.
You may choose to be patient, put up with the inconveniences and risks of your basement tunnel until you can install that trusted door. Or, you may simply decide that what comes through the tunnel isn't remotely worth the aggravation it creates and dynamite the whole thing, reclaiming your basement for yourself.
Is it time to start thinking about abandoning the Internet? Well, I've pondered that option at some length, and I'm not alone. Donald Knuth, who's always at least a decade ahead of everybody else, abandoned E-mail on January 1st, 1990, saying “Email is a wonderful thing for people whose role in life is to be on top of things. But not for me; my role is to be on the bottom of things.” Harry Schultz, one of the wisest observers of the financial and geopolitical scene, advised abandoning E-mail in favour of FAX more than a year ago. While few people have explicitly announced their retirement from the Internet, I suspect that more and more parents are loath to provide Internet access to their children, knowing that their mailboxes will be filled every day with hundreds of disgusting messages. People of all sorts simply walk away from the Internet after suffering the repellent pop-ups and attacks by spyware installed on their computers. You won't see this as a downturn in people on the Internet, at least right away, but keep your eye on the second derivative.
Another trend I expect to emerge is an attempt to re-create the Internet of a decade ago by erecting virtual barriers to keep out the rabble. When I'm feeling down I call it “Internet Gated Communities”, when in an optimistic mood, “The Faculty Club”. This may lead to what many observers refer to as “the Balkanisation of the Internet”—a fragmentation of the “goes everywhere, reaches everybody” vision of the global nervous system into disconnected communities. This may not be such a bad thing. Yes, we will not end up with a ubiquitous global wired community. But if you want to get an idea what that might actually look like, here's a little experiment you can try. Turn off your spam filter and read all the spam you get in a day, including visiting the Web sites they direct you to. Now imagine that, multiplied by a factor of about a hundred. Welcome to the electronic global slum! I am one of those despicable people who believe that IQ not only exists but matters. From the origin of the Internet through the mid 1990s, I'd estimate the mean IQ of Internet users as about 115. Today it's probably somewhere around 100, the mean in Europe and North America. The difference you see in the Internet of today from that of ten years ago is what one standard deviation (15 points) drop in IQ looks like. But the mean IQ of the world is a tad less than 90 today, and it's expected to fall to about 86 by 2050. So, when the digital divide is conquered and all ten billion naked apes are wired up, you're looking at about another standard deviation's drop in the IQ of the Internet. Just imagine what that will be like.
Optimists point to initiatives underway to address the problems of the Internet: secure operating systems, certificate based authentication, tools for identifying abusers and legal sanctions against them, and the like. But I fear the cure may be worse than the disease, so much so that I penned a 25,000 word screed sketching the transformation of the Internet from an open network of peers to a locked-down medium for delivering commercial content to passive consumers.
I'm not ready to abandon the Internet, at least not right away. But I'm thinking about it, and I suspect I'm not alone. Those who have already abandoned it are, by that very choice, neither publishing Web pages nor posting messages about it; they are silent, visible only by their absence from the online community. Will early adopters of the Internet, who are in the best position to compare what it is today with what they connected to years ago, become early opters-out? Me, I'm keeping an eye on this trend—it could just be the next big thing.
| Flash! Within twelve hours of my posting this document, CNN ran a story titled: Gangs Used Internet to Plan Street Fight. You can't make up stuff like this. Thanks to Mike Sisk for pointing this out. |
|
|